Threat Modelling and Automated Attack Simulations
Risk Exposure
“Can we determine the risk posture of our applications?”
We provide a comprehensive solution that captures a digital model of your IT/OT/Cloud infrastructure assets together with its security parameters and run simulations to identify all attack paths, risk exposure and shortest time to compromise.
Risk Migitation
Our attack simulations will identify the critical attack paths and chokepoints where mitigation is most effective.
Risk Prediction
“Can I predict how infrastructure changes will affect my risk posture?”
With our solution you can run simulations to predict how your risk posture will change BEFORE making any changes to your IT/OT/Cloud infrastructure.
Discover Your Weak Spots
securiCAD assesses the robustness and risk exposure of your IT architecture by revealing both technical and structural vulnerabilities.

Manage Cyber Risk with Automation & AI
Challenge
- Scale and speed drives complexity
- Cyber risks are rising and growing regulatory demands
- Threat modeling lacks automated tools and capabilities to simulate
Solution
- AI-based simulations enables continuous and automatic mitigations
- Quantify holistic security posture and continuously risk monitoring, perfectly matched for Continuous Delivery and DevOps
- Security by design early in the development process and continuously throughout the system lifecycle (Shift-Left)
Addresses Key Security Trends
Cyber moves to C-level, requiring risk-based approach
- Cyber is top risk for businesses, and rapidly increasing spend
- Huge need to manage cyber in a business minded way, requiring a risk based approach (McKinsey)
- foreseeti awarded as Category Leader in Cyber Risk Quantification Solutions
Simulations are one of the fastest growing areas in cyber
- Breach and Attack Simulations in innovation phase of Gartner hype cycle, now growing at +40% CAGR
- foreseeti awarded as Innovator in Simulation Solutions and provides the most automated threat modelling solution in the market
Rapid adoption of Cloud, DevOps and DevSecOps
- The rapid adoption of cloud, agile, and DevOps puts new requirements and potential on cyber
- foreseeti has now applied our leading technology for Cloud, unleashing the potential of DevOps and DevSecOps in practice
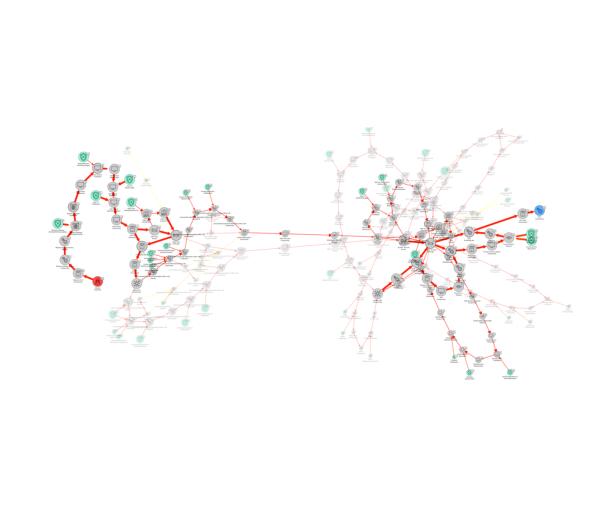
Find, Prioritise & Mitigate Weaknesses
- Based on the simulation, securiCAD will generate reports on risks exposure, threats and weaknesses and critical attack paths
- Critical paths exposes top threats, weaknesses, misconfigurations, chokepoints, exploited vulnerabilities and potential mitigations
- securiCAD will also suggest mitigations and security controls that can lower the risk exposure which can be applied and evaluated in the model

